Describe Four Hardware Methods Used to Protect Data
Take action today to secure your data at rest in use and in motion to ensure your organization doesnt end up on this list. The keys used to decipher the text can be 128- 192- or 256-bit long.

Protect Data In Transit Or At Rest Ibm Cloud Architecture Center
Hard drive life is.
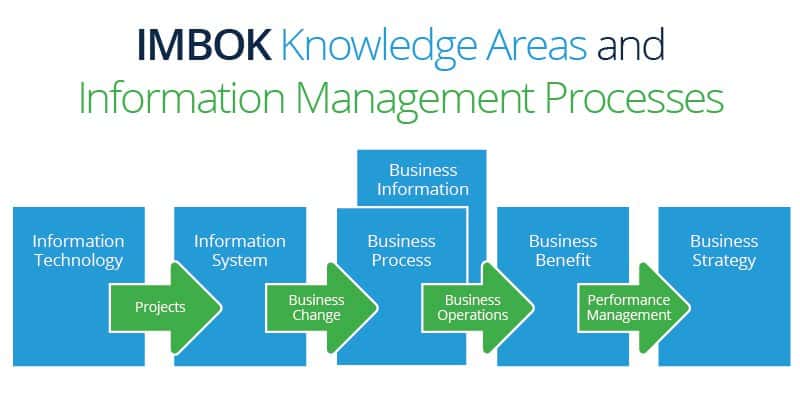
. This could help when there is a crash following a cyber attack and also when a device is lost or gets stolen. Describe How Hardware Software And Data Can Be Protected From Potential Threats. Passwords are essential to guard your information.
Hardware systems can provide. If an employee leaves your. In this paper we propose a hardware - based ar chitecture to protect the confidenti ality and integrity.
Here are ten ways to protect your data and your companys security. So basically Bare register store the starting address of program and limit register store the size of the process so when a process wants to access the memory then it is checked that it. High-risk data is the prime candidate for encryption every step on the way.
There are also services to help track stolen items. Secure Email and File Transfer Corporate Practices 3rd Annual Survey Results. Up to 24 cash back 33 I can develop solutions to improve my own productivity in using IT.
Software left outdated may still contain security flaws that can leave you susceptible to a data or privacy breach. Tape is still commonly used today for large enterprise system backup archiving and even for long-term cloud storage. Less common examples include hardware security modules which provision cryptographic keys for critical functions such as encryption decryption and authentication for various systems.
Making stronger passwords is necessary for fighting a number of password hacking tools that are easy to get on the market. This is one of the most important things to be done. Many hardware manufacturers include a Kensington Security Slot in the design of desktops laptops monitors projectors printers servers and other equipment.
Keeping hardware safe is also essential for data security. Your computer must be properly patched and updated. Windows 2000 XP Pro and Server 2003 support the Encrypting File System EFS.
Email Statistics Report 20152019. Here are some of the common encryption methods that you might see used in various encryption tools. Try ensuring that there are a combination of different characters including alphabets numbers symbols and other capital letters.
Mr Mohr has seen me doing this. Traditional tape or disk backup. Rename your admin and root accounts to something else.
Laptops are portable so there is a higher risk that they can be stolen. My password are in place and of reasonable strength. Tape backup has been around in some form or another since the 1960s.
Of data at run - time. On your phone lock it with a strong password and. Using Kensington locks to physically secure equipment securing server rooms and putting away mobile devices can prevent theft.
For example Microsofts Bitlocker comes free with its newest editions. Password-protect your computing devices. 34 Inference controls 4.
Embrace security by obscurity. You can use this built-in certificate-based encryption method to protect individual files. Implementing a strategy for strong logins and passwords to your network data is crucial for protecting your data.
A password should be carefully chosen to be secure and not easily guessed by someone else. 4 Updating is important. Common examples include hardware firewalls and proxy servers.
Creating strong passwords and never using the same password across sites or devices is one of the best things you can do to protect yourself from digital invasion. Data access is also much faster with disk-storage methods. As a consequence it is important to take more security measures in order to protect all laptops.
A combination of numbers letter and capital letters is better than a simple word that can be guessed. The backup can be done on an external hard drive portable storage device or. Have data backup update it regularly.
Hard Drive or External Hard Drives- You can piggy back an additional hard drive to your computer. Up to 24 cash back 15 I can describe ways to protect hardware software and data and minimize security risk. Tape-storage methods are still a cheaper option by two-thirds compared to hard disks.
Advanced Encryption Standard AES Advanced Encryption Standard is a symmetric encryption algorithm that encrypts fixed blocks of data of 128 bits at a time. This stops access to your network on stolen devices. 15 I can describe ways to protect hardware software and data and minimise security risk.
Using a hardware solution is costlier than its software option because it needs a dedicated storage space. Hardware security can pertain to a device used to scan a system or monitor network traffic. Sensitive data in an organization should be locked away with strong passwords.
5 Secure every laptop. However hard drives are more versatile and better-suited to small scale operations. Here are a few tips that will help minimize the damage if it happens to you.
Cable locks are a common method of protecting laptops and other equipment from thieves. While it sounds obvious if anyone steals your device they will have to. Cryptography 51 Basic cryptographic technologies 52 Uses of cryptography 53 Applications of cryptography Acknowledgements Glossary Bibliography Summary Data security refers to the protection of information against possible violations that can.
USB-Flash Drives Flash Drives make a quick backup option. In order to preven t the attacker from stealing the confidential or. Recent updates allow your Data to be more secured.
You can attach Kensington and other brands of compatible cable locks into the slot. 34 I can test solutions to check that they work as intended. Keep a backup of all data especially sensitive and critical data.
Implement anti-virus anti-spam and anti-spyware tools on the gateway andor at the host-level. Install internal protection protocols First and foremost you must train your employees to protect your internal systems. Not only are they reasonable but.
The primary benefits of tape are massive capacity low cost and offsite data backup.

Protect Data In Transit Or At Rest Ibm Cloud Architecture Center

Data Storage Security How Secure Is Your Data Hypertec Direct
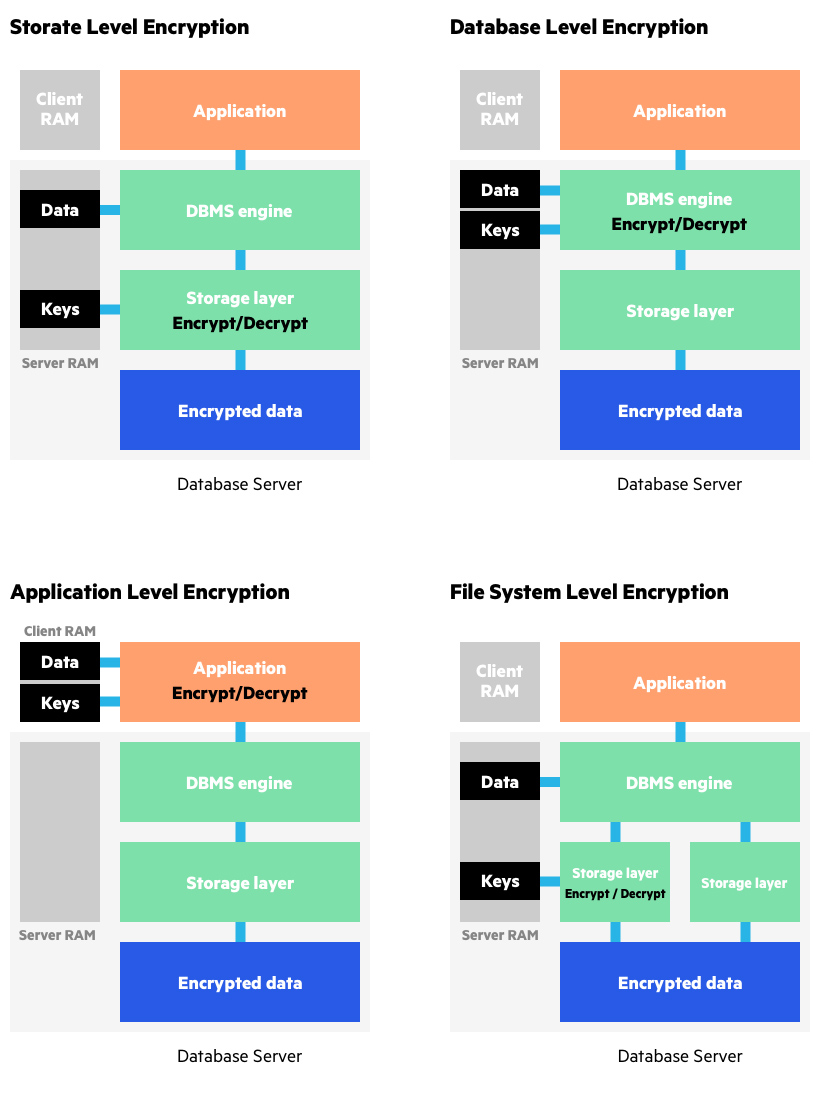
What Is Data Encryption From Des To Modern Algorithms Imperva

Cybersecurity 101 Protect Your Privacy From Hackers Spies And The Government Zdnet

Information Management Best Practices Smartsheet

Chapter 6 Information Systems Security Information Systems For Business And Beyond

Secure Portable Drives Protect Your Data On The Go B H Explora

Data Security Methods And How To Protect Data
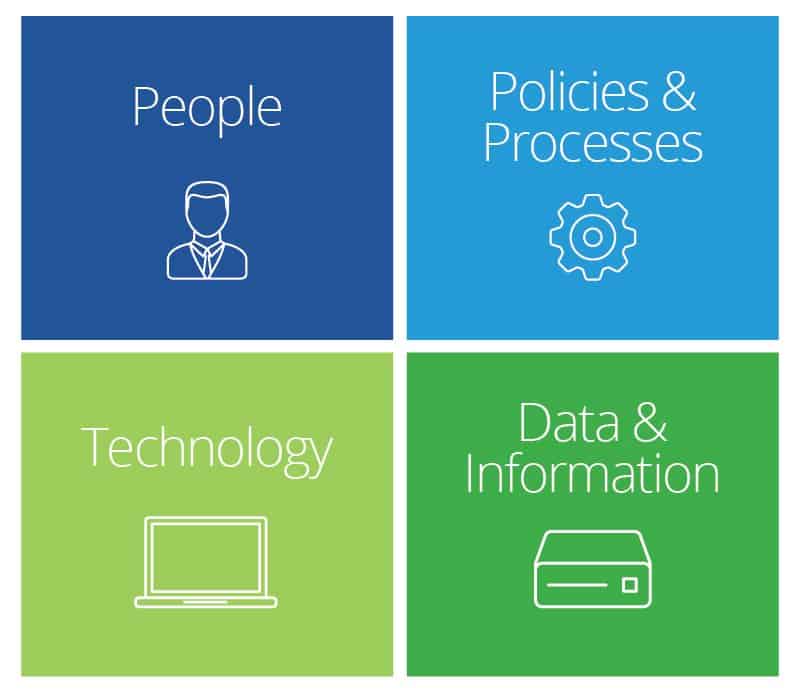
Information Management Best Practices Smartsheet

Physical Security Of A Data Center

1 2 Identifying The Components Of Information Systems Workforce Libretexts
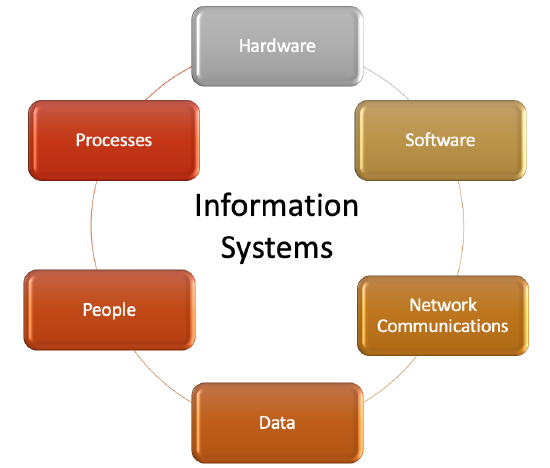
1 2 Identifying The Components Of Information Systems Workforce Libretexts

7 Easy Steps To Take To Protect Your Data

Top 10 Firewall Hardware Devices For 2021 Toolbox It Security

Protect Data In Transit Or At Rest Ibm Cloud Architecture Center

The 10 Data Security Measures You Must Take For Your Business Wimi


Comments
Post a Comment